Note: This article refers to the Framer desktop app. Learn more about the differences between the Framer web and desktop app here.
When we introduced Framer to the web, we aimed to bring the features we love from Framer X directly to the browser, as the browser also allows us to introduce an array of new features such as multiplayer and collaboration.
What happens to Framer X?
Americanflat Collage Picture Frame in Black MDF with Three Displays of 5' x 7' Wood with Lead Free Glass for Wall - 8' x 16' Americanflat New at target ¬ $58.99 - $185.99. Poster frames are a surefire way to add style to your home. First and foremost, a quality poster frame does exactly what it says on the tin: frames a poster. But beyond that, it is a smart method of elevating a room. After all, a framed poster always looks more classy than one tacked to the wall.
Framer Web is not a successor of Framer X, but rather an alternative to the macOS-only desktop client.
Framer X as a macOS desktop app will continue to exist next to Framer Web and will be available to those on the Pro or Enterprise plan.
The only change is that Framer X will be renamed to Framer, and will be referred to as the Desktop version whenever a distinction is made.
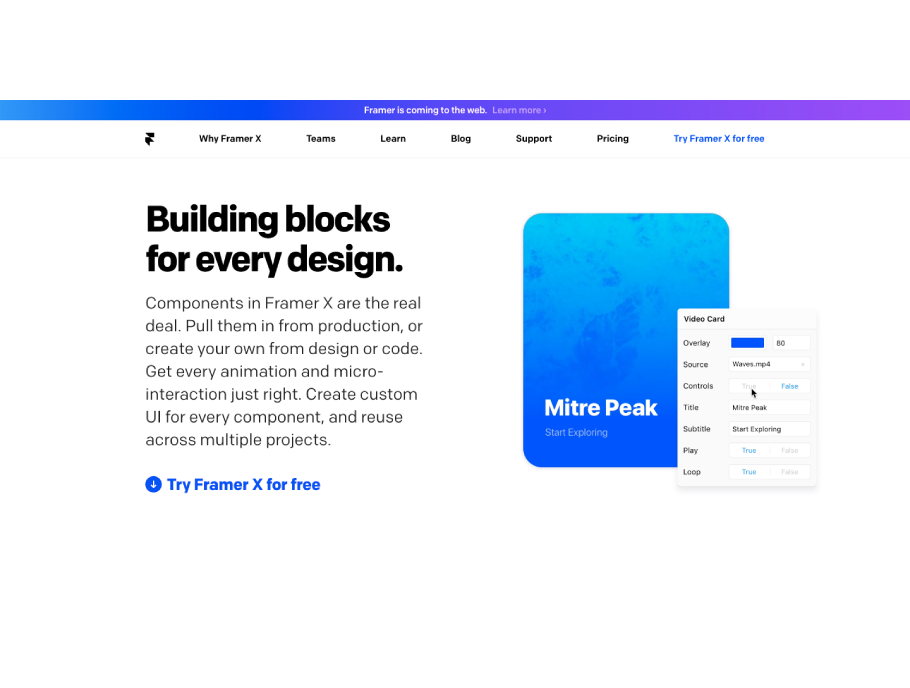
You can open any files created in Framer X, in Framer Desktop.

Download the Framer Desktop app here
The Framer Desktop client is not an automatic upgrade from Framer X, download the Framer Desktop application here.
What happens to my existing license for Framer X?
Any active licenses for Framer X will be grandfathered into our new licensing system.
Will features from Framer Web come to the desktop app?
Generally the desktop and web platforms will stay in sync. Framer will be largely the same experience regarding the interface and all the prototyping and design tools you have at your disposal.
However, some features are limited by the platform on which Framer lives and may be available to just the web or desktop client for the foreseeable future.
Where can I find an overview of the differences between desktop and web?
To find an overview of all the differences between the two versions, head on over to this article.

HTTP security headers provide yet another layer of security by helping to mitigate attacks and security vulnerabilities by telling your browser how to behave. In this post we will be diving more in-depth into X-Frame-Options (XFO), which is a header that helps to protect your visitors against clickjacking attacks. It is recommended that you use the X-Frame-Options header on pages which should not be allowed to render a page in a frame.
What is X-Frame-Options?
X-Frame-Options (XFO), is an HTTP response header, also referred to as an HTTP security header, which has been around since 2008. In 2013 it was officially published as RFC 7034, but is not an internet standard. This header tells your browser how to behave when handling your site's content. The main reason for its inception was to provide clickjacking protection by not allowing rendering of a page in a frame. This can include rendering of a page in a <frame>, <iframe>, or <object>. Iframes are used to embed and isolate third party content into a website. Examples of things that use iframes might include social media sharing buttons, Google Maps, video players, audio players, third party advertising, and even some OAuth implementations.
How widely is the X-Frame-Options header being used? Scott Helme did an interesting case study back in February 2016. He analyzed the security headers of the top 1 million sites, according to Alexa, and this is what he found. It is shown as XFO below in the chart. Only 7.6% of the top sites are utilizing the header.
While it is good to see increases across the board for not only the XFO header, but all security headers, the overall usage is very low. More sites need to start taking advantage of HTTP security headers.
Clickjacking
So what exactly is clickjacking? Clickjacking is an attack that occurs when an attacker uses a transparent iframe in a window to trick a user into clicking on a CTA, such as a button or link, to another server in which they have an identical looking window. The attacker in a sense hijacks the clicks meant for the original server and sends them to the other server. This is an attack on both the visitor themselves and on the server.
Here are a couple possible known exploits or uses for clickjacking.
- Tricking users into making their social networking profile information public
- Sharing or liking links on Facebook
- Clicking Google Adsense ads to generate pay per click revenue
- Making users follow someone on Twitter or Facebook
- Downloading and running a malware (malicious software) allowing to a remote attacker to take control of others computers
- Getting likes on Facebook fan page or +1 on Google Plus
- Playing YouTube videos to gain views
Clickjacking is easy to implement, and if your site has actions that can be done with a single click, then most likely it can be clickjacked. It might not be as common as cross site scripting or code injection attacks, but it is still another vulnerability that exists. Sometimes it helps to see a visual. Below is a clickjacking demo using both transparent and non-transparent iframes.
Here is another good live example in which you can see a demonstration of clickjacking.
X-Frame-Options directives
The X-Frame-Options header has three different directives in which you can choose from. These must be sent as an HTTP header, as the browser will ignore if found in a META tag. It is also important to note that certain directives are only supported in certain browsers. See browser support further below in this post. While it is not required to send this response header across your entire site, it is best practice to at least enable it on pages that need it.
1. deny directive
The deny directive completely disables the loading of the page in a frame, regardless of what site is trying. Below is what the header request will look like if this is enabled.
This might be a great way to lock down your site, but it will also break a lot of functionality. The following two directives below are more common use cases for a typical website.
Examples of sites currently using the deny directive:
- GitHub
2. sameorigin directive
The sameorigin directive allows the page to be loaded in a frame on the same origin as the page itself. Below is what the header request will look like if this is enabled.
We have the sameorigin directive enabled on this website. With this directive enabled, only our website is allowed to embed an iframe of one of our pages. This is probably the most commonly used directive out of the three. It is a good balance between functionality and security.
It is also important to note that if a browser or plugin can not reliably determine whether the origin of the content and the frame have the same origin, this must be treated as deny.
Examples of sites currently using the sameorigin directive:
- Amazon
- eBay
3. allow-from uri directive
The allow-from uri directive allows the page to only be loaded in a frame on the specified origin and or domain. Below is what the header request will look like if this is enabled.
This allows you to lock down your site to only trusted origins. But be careful with this directive. If you apply it and the browser does not support it, then you will have NO clickjacking defense in place.
Enabling X-Frame-Options header
The X-Frame-Options header is easy to implement and only requires a slight web server configuration change. You might also want to check to make sure you don't already have the header enabled. Here are a couple easy ways to quickly check.
- Open up the Network panel in Chrome DevTools and if your site is using a security header it will show up on the Headers tab.
- Another quick way to check your security headers is to quickly scan your site with a free tool, securityheaders.io, created by Scott Helme. This gives you a grade based on all of your security headers and you can see what you might be missing.
Enable on Nginx
To enable the X-Frame-Options header on Nginx simply add it to your server block config.
Enable on Apache
To enable on Apache simply add it to your httpd.conf file (Apache config file).
Enable on IIS
To enable on IIS simply add it to your site's Web.config file.
X-Frame-Options browser support
It is important to realize that not all browsers support the allow-from directive. So be careful if you are using that. All modern browsers do support the deny and sameorigin directives. For legacy browsers, such as IE7 for example, your best solution currently is to use what they call a frame-breaker or frame-buster.
Grammar Xl
| Browser | deny / sameorigin support | allow-from support |
|---|---|---|
| Chrome | 4.1+ | No |
| Edge | Yes | Yes |
| Firefox | 1.9.2+ | 18.0+ |
| Internet Explorer | 8.0+ | 9.0+ |
| Opera | 10.50+ | No |
| Safari | 4.0+ | No |
Framer X Vs Figma
Another newer option and or alternative you have to using XFO is to use the Content Security Policy and frame-ancestors directive. This will most likely eventually replace XFO altogether. One major benefit to this directive is that it allows you to authorize multiple domains. However, it is not supported in all browsers yet, Chrome 39+ and FF 33+ support it, but there is no support for Internet Explorer. You could however use both the X-Frame-Options and frame-ancestors together.
Summary
Framer X Npm
Hopefully now you understand a little more about what the X-Frame-Options HTTP response header does and how it can help prevent clickjacking. As seen above, this is very easy to implement. We use security headers on our websites and we encourage you to do the same. Together we can make the web a more secure place and help boost the security header usage numbers.
